A thorough understanding of mobile security risks is crucial for both personal and business users, particularly in today’s environment, where the use of mobile devices in corporate settings is widespread. Mobile devices frequently contain sensitive business data and provide access to organizational networks, making them appealing targets for cyberthreats, which can result in anything from data breaches to operational disruptions.
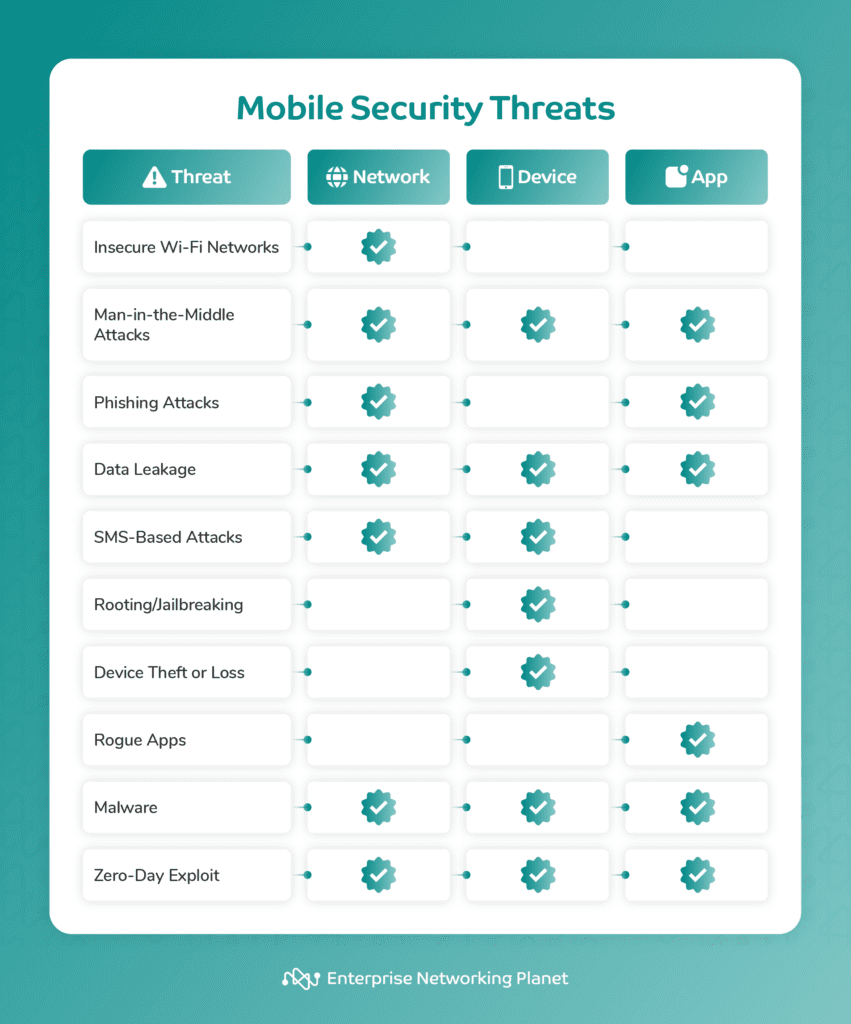
Below is an overview of top 10 mobile security threats and what they specifically target: networks, devices, or applications.
Mobile network security threats
Mobile network security threats include insecure Wi-Fi networks, man-in-the-middle (MITM) attacks, phishing attacks, and data leakage. Some of these threats can be classified under multiple categories as they target several components.
Insecure Wi-Fi networks
Type of mobile threat: Network
Insecure Wi-Fi networks are susceptible to exploitation, allowing attackers to intercept data transmissions and gain unauthorized access. Cybercriminals use techniques like eavesdropping or setting up rogue Wi-Fi hotspots to illegally access systems, launch MITM attacks, or intercept transmission of sensitive data.
Best defense
Use secure, password-protected Wi-Fi networks, enable WPA3 encryption, and make use of a virtual private network (VPN) to add a layer of security when you’re connecting to public Wi-Fi.
Man-in-the-middle attacks
Type of mobile threat: Network, device, and app
MITM attacks involve intercepting and monitoring communication between two parties without their knowledge through packet sniffing, DNS spoofing, or setting up untrustworthy Wi-Fi hotspots. This allows attackers to gain unauthorized access to sensitive information, compromising user privacy and security.
MItM attacks are primarily a network threat since attackers target network communications. However, these attacks can also expose sensitive data stored on the devices connected to the compromised network. In terms of apps, a cybercriminal could intercept communication between apps and a server over an insecure network and access confidential information or inject malicious data.
Best defense
Use encrypted connections like HTTPS, avoid accessing sensitive information on public networks, and consider using a mobile VPN for added security. Additionally, keep your devices and apps up-to-date and be cautious of any unexpected changes in the behavior of your device or apps.
Phishing attacks
Type of mobile threat: Network and app
During phishing attacks, bad actors trick you into revealing sensitive information. They use fraudulent apps or messages to impersonate legitimate sources to coax you to give out passwords, credit card details, or other confidential data.
Best defense
Verify the legitimacy of websites and apps before sharing your personal information and enable two-factor authentication (2FA) or multi-factor authentication (MFA) on your mobile device for added security. Also, be sure to keep everyone in your organization trained and informed about phishing attacks and other social engineering threats.
Data leakage
Type of mobile threat: Network, device, and app
Data leakage refers to the unauthorized transmission of sensitive data from an organization to an external recipient. This typically happens because of unencrypted connections or when apps have excessive permissions that let them access and share user data without consent. Data leakage exposes personal or corporate information, leading to privacy breaches.
On the network level, data leakage can occur when unwanted individuals access private information being transmitted over the network due to weak network security protocols or compromised network devices.
Data leakage in devices happens when confidential data stored on the device is accessed by attackers through malware, physical theft of the device, or weak mobile security settings.
In terms of apps, this threat can take place when an app unintentionally reveals sensitive data as a result of coding errors or weak security controls.
Best defense
Regularly review and manage app permissions, use encrypted connections on public networks, and be cautious about sharing sensitive information on unsecured platforms.
Mobile device security threats
Security threats in mobile devices include SMS-based attacks, rooting or jailbreaking, and device theft and loss. Some of these attacks also can also fall under multiple categories.
SMS-based attacks
Type of mobile threat: Device and network
SMS-based attacks exploit weaknesses in SMS to deliver malware or phishing links, jeopardizing device security. Attackers send deceptive SMS messages containing malicious links or instructions, tricking you into taking actions. Clicking on links in these messages may lead to phishing websites or install malware, potentially allowing unauthorized access or data compromise.
SMS-based attacks often target individual devices to steal sensitive data, send premium-rate SMS messages without your knowledge, or carry out other malicious activities.
These attacks could potentially be used to execute a Denial-of-Service (DoS) attack over networks, too. By sending a large volume of SMS messages to a single target, an attacker could overload the network or device, rendering it unusable.
Best defense
Be wary of SMS messages from unknown numbers or those that request personal information, avoid clicking on links from unknown sources, and use mobile security apps that detect and block malicious content.
Rooting/jailbreaking
Type of mobile threat: Device
Rooting (Android) or jailbreaking (iOS) involves bypassing the manufacturer-imposed limitations on device functionality, which inherently compromises the device’s security model. Some users deliberately do this to obtain root access and alter system files. However, this practice weakens device security, increasing its vulnerability to malware and unauthorized access.
Best defense
Avoid rooting or jailbreaking your device, as it exposes it to additional security risks. Keep your device software updated and only use trusted apps from official sources.
Device theft or loss
Type of mobile threat: Device
Unauthorized data access can occur when your mobile device gets lost or stolen, especially if it lacks proper security measures, like strong passwords or biometric authentication.
Best defense
Implement strong authentication methods, encrypt your device, enable remote tracking and wiping functionalities, and avoid storing sensitive information directly on your device.
Mobile application security threats
Mobile app security threats include rogue apps, malware, and zero-day exploits. Malware and zero-day exploits can be categorized under multiple types of mobile threats.
Rogue apps
Type of mobile threat: App
Rogue apps are counterfeit mobile applications frequently used in mobile network hacking. These apps mimic trusted applications with the goal to steal sensitive information, such as login credentials or bank details. They can also install malware, spyware, or ransomware on your device.
You may unknowingly install rogue apps through various channels, like unofficial app stores, email links, repackaged apps in official stores, and even fake app stores.
Best defense
Only download apps from official app stores, review app permissions before installation, keep your mobile OS updated, and use reputable mobile security apps.
Malware
Type of mobile threat: App, device, and network
Malicious software, or malware, is a versatile threat that can target and exploit vulnerabilities at multiple levels. It can take the form of viruses, worms, Trojan horses, or spyware, and has the potential to undermine the security of mobile devices.
Malware typically enters devices when you accidentally download apps with malicious intent, access websites that lack security, or open attachments that carry infections. This can then disrupt your device’s functionality, lead to the theft of sensitive information, or enable unauthorized tracking of user activities.
Malware can spread across networks, impact operations, or put data being transmitted over the network at risk. Furthermore, it can spread to individual devices, weakening their security and making them vulnerable to data theft. Malware can also target specific apps and take advantage of weak spots in their code to illegally access data processed or stored by the app.
Best defense
Install reputable antivirus and anti-malware software on your device, update your mobile OS and apps regularly, and download apps only from official app stores.
Zero-day exploits
Type of mobile threat: App, device, and network
Zero-day exploits represent a significant security risk, as they take advantage of vulnerabilities in software or apps that are unknown to the vendor. Attackers exploit these vulnerabilities before the vendor can release patches or updates, leading to a range of potential security issues.
These threats exist on multiple levels. On a network level, cybercriminals can use them to penetrate network defenses, potentially gaining access to private information or assuming control over network operations. On a device level, zero-day exploits bypass device security measures, which could lead to the installation of malware or theft of personal data.
In the context of apps, these threats can take advantage of unpatched vulnerabilities in an app’s code, resulting in unwanted access or data breaches.
Best defense
Always update your software and apps to the latest versions, use security software to detect and mitigate potential threats, and follow security advisories from software vendors to apply patches promptly.
General tips for defending against mobile threats
There are several steps you can take to bolster mobile security and defend against mobile threats, such as keeping your software updated, using strong authentication, practicing good app security, protecting network communications, installing security software, and being wary of phishing attempts.
Keep your software updated
Regularly updating your device’s OS and apps is imperative for maintaining security. Updates commonly include patches for security vulnerabilities discovered since the last version of the software was released. By not updating, you leave your device exposed to these vulnerabilities. We recommend enabling automatic software updates whenever possible to ensure quick installation.
Use strong authentication
Using strong login passwords/PINs and biometric authentication, like fingerprint or facial recognition, can help protect your device from unauthorized access. 2FA of MFA, which requires multiple forms of verification aside from your password, further strengthens security. NIST’s Digital Authentication Guideline provides policies for Federal agencies implementing authentication, including the use of strong passwords/PINs and 2FA.
Practice good app security
Download apps only from official app stores, as third-party app stores may not have the same security measures in place. Additionally, regularly review and delete apps that you no longer use or need because these can be potential security risks.
Also be mindful of the personal information you allow apps to access. CISA recommends disabling third-party app stores and using security container technology to isolate enterprise data.
Protect network communications
Disable network radios like Bluetooth, NFC, Wi-Fi, and GPS when they’re not in use to reduce potential attack vectors. Moreover, avoid using public Wi-Fi networks when possible, as they can be insecure and exploited by cybercriminals. Here are a few simple steps to help you secure your networks, including wireless and remote access.
Install security software
Installing security software on your mobile device can effectively protect it from malware, and enhance overall mobile network security. Mobile security software is a broad term that covers the following:
Mobile content management (MCM)
Mobile content management (MCM) solutions manage and secure mobile content such as documents, images, and videos.
Mobile identity management (MIM)
Mobile identity management (MIM) tools authenticate and authorize mobile users and devices.
Antivirus/anti-malware software
Antivirus and anti-malware software detects and removes malware from mobile devices.
Mobile threat defense (MTD)
Mobile threat defense (MTD) solutions actively safeguard against mobile attacks by continuously monitoring and thwarting threats originating from malicious apps, networks, or devices.
Mobile VPN
Mobile VPNs encrypt and safeguard mobile data traffic, ensuring secure and private communication over public networks.
Firewall
Firewalls block unauthorized access to mobile devices or networks.
Mobile application management (MAM)
Mobile application management (MAM) software controls and protects mobile apps and data and allows administrators to manage the entire lifecycle of an app. This includes everything from app deployment and updates to policy enforcement and app retirement, ensuring a secure and efficient mobile environment.
Mobile device management (MDM)
Mobile device management (MDM) solutions give centralized control over mobile devices, letting administrators enforce security policies, manage device settings, and monitor device usage to ensure the security and integrity of corporate data.
Beware of phishing attempts
Always check the legitimacy of an email before opening any attachments or clicking on any links. Phishing emails often imitate legitimate companies or services to trick you into sharing sensitive information. Be particularly wary of emails in your junk or spam folders. Here are a few best practices to prevent phishing attacks.
12 signs your device is compromised
You can look out for some signs that your device is compromised, like unauthorized activities, unusual network traffic, unfamiliar apps, strange pop-ups, unexpected data usage, rapid battery drain, slow performance, overheating, unfamiliar texts or calls, changes in settings, inability to update, and difficulty shutting down.
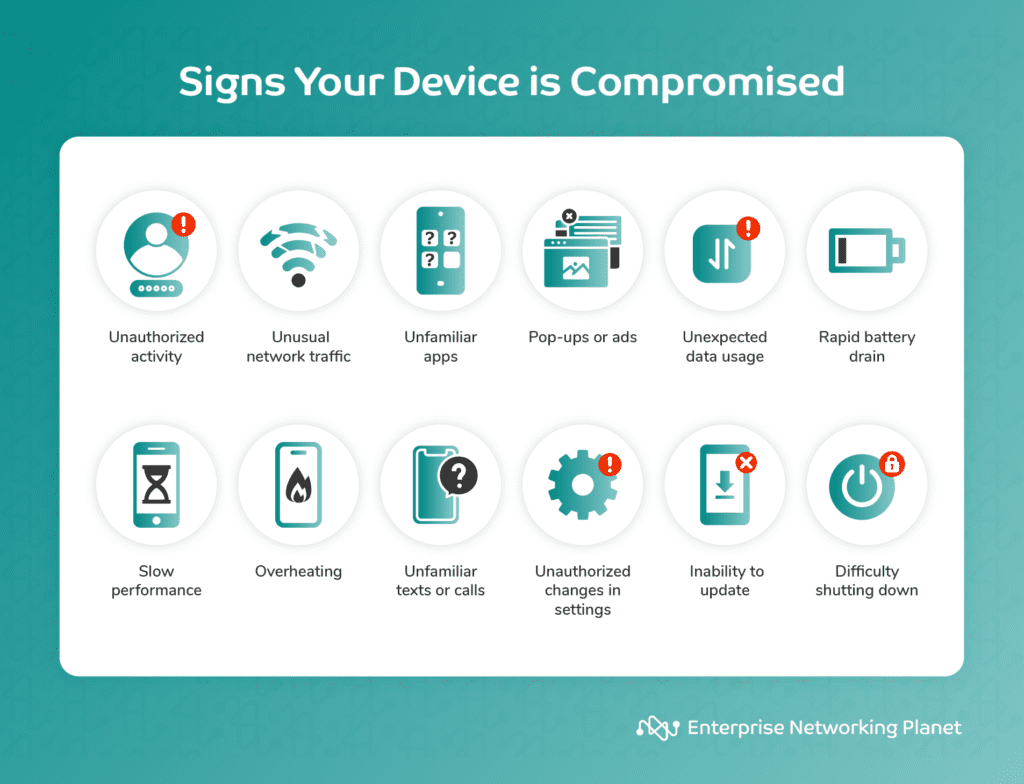
- Unauthorized activities: Unusual login activity, unrecognized devices, or unexpected login alerts may suggest your accounts are at risk.
- Unusual network traffic: Large data transfers at odd times, or when you’re not using your device, could hint at a security issue.
- Unfamiliar apps: Apps or software you didn’t install, or altered app settings, could mean your device is compromised.
- Strange pop-ups, ads, emails, or messages: Unexpected notifications, especially urging you to click links or download files, or suspicious emails/messages, may signal malware.
- Unexpected data usage: Sudden increases in data usage could mean a malicious app is transmitting data.
- Rapid battery drain: Faster battery drain could be due to malware or other malicious activities consuming resources.
- Slow performance: Frequent freezes, crashes, or sluggishness could be a sign of malware or unauthorized processes running in the background.
- Overheating: Excessive heat despite light use could indicate background malware processes.
- Unfamiliar texts or calls: Unknown texts, calls, or messages, particularly with links or personal information requests, could be a sign of phishing attempts.
- Changes in settings: Changes in your device settings, unknown accounts, or disabled/uninstalled security software could suggest a security breach.
- Inability to update: If you can’t update your OS or apps, your device’s security might be compromised.
- Difficulty shutting down: If your device refuses to shut down or restart it could be due to malicious processes resisting termination.
What to do if your device is infected
In the unfortunate event that your device is infected, there are actionable steps you can undertake to rectify the situation, such as isolating your device, running a security scan, removing malicious apps, updating your OS, changing your password, enabling 2FA or MFA, reviewing account activity and monitoring unusual behavior, restoring from backup, installing mobile security apps, resetting your device to factory settings, seeking professional assistance, and educating yourself and your teammates.
- Isolate your device: Disconnect your device from the internet and disable Wi-Fi and mobile data to prevent further communication with the attacker or the spread of malware.
- Run a security scan: Use a reliable antivirus or anti-malware app to run a thorough scan of your device. Ensure that the security software is up-to-date before initiating the scan.
- Remove malicious apps: Identify and uninstall any suspicious or unfamiliar apps from your device. Check your app list and remove anything that you didn’t intentionally install.
- Update your operating system: Ensure that your device’s OS is up-to-date. Install any available updates and patches to address vulnerabilities that may have been exploited by the malware. If possible, enable automatic OS and app updates.
- Change passwords: Change the passwords for all your accounts, especially those related to sensitive information or financial transactions. Choose strong, unique passwords for each account and avoid using easy-to-guess passwords.
- Enable 2FA or MFA: If not already enabled, set up 2FA or MFA for your important accounts for boost security.
- Review account activity and monitor unusual behavior: Review your account activity thoroughly and look for any suspicious transactions, and report any unauthorized access to your service providers. Additionally, keep a close eye on your device for any unusual behavior, pop-ups, or performance issues. Regularly review your app permissions and settings to ensure they align with your preferences.
- Restore from backup: If you have a recent backup of your device, restore it to a state before the infection occurred to help eliminate any traces of malware that may persist on your device.
- Install mobile security apps: After resolving the infection, install a trusted mobile security app for ongoing protection. Keep the app updated to defend against emerging threats.
- Reset your device to factory settings: If the infection is severe and cannot be remedied through other means, consider resetting your device to factory settings as a last resort. Doing so will erase all data, including the malware, but make sure to back up essential data before taking this step.
- Seek professional assistance: If you’re unsure about the extent of the infection or if you’re unable to remove the malware, consider seeking assistance from a professional or contacting your device’s customer support.
- Educate yourself and your team: Learn from the experience and understand how the malware infected your device to avoid similar situations in the future. Stay informed about the latest security threats and best practices, and make sure anyone else using your network understands risks and best practices as well.
Bottom line: Staying ahead of mobile security threats
Mobile security threats are everywhere, and in many cases they’re harder to spot or prevent than on traditional computers. But by remaining informed, proactive, and vigilant, you can avoid the vast majority of threats and attacks on your mobile networks, devices, and apps.
Using mobile VPNs is an effective way to protect your devices from mobile security threats. Read our guide on the best mobile VPNs for every use case to find out which providers to trust for your business and personal security needs.
Source link

Leave a Reply