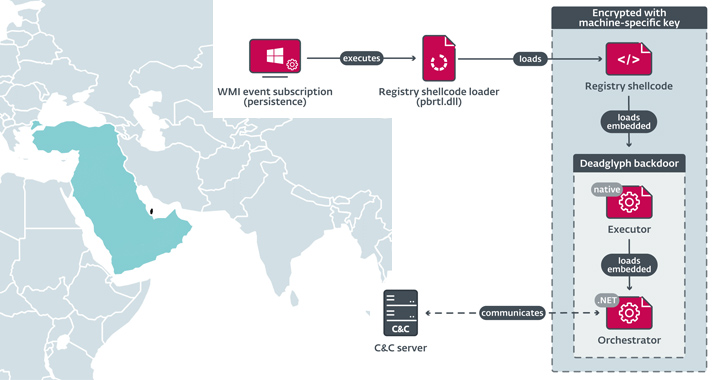
Sep 23, 2023THNCyber Espionage / Malware Cybersecurity researchers have discovered a previously undocumented advanced backdoor dubbed Deadglyph employed by a threat actor known as Stealth Falcon as part of a cyber espionage campaign. “Deadglyph’s architecture is unusual as it consists of cooperating components – one a native x64 binary, the other a .NET assembly,” ESET […]
ESET’s cutting-edge threat research at LABScon – Week in security with Tony Anscombe
Video Two ESET malware researchers took to the LABScon stage this year to deconstruct sophisticated attacks conducted by two well-known APT groups 22 Sep 2023 The lineup of speakers at this year’s edition of LABScon featured two ESET malware researchers who took to the stage to deconstruct sophisticated attacks conducted by two well-known APT groups. […]