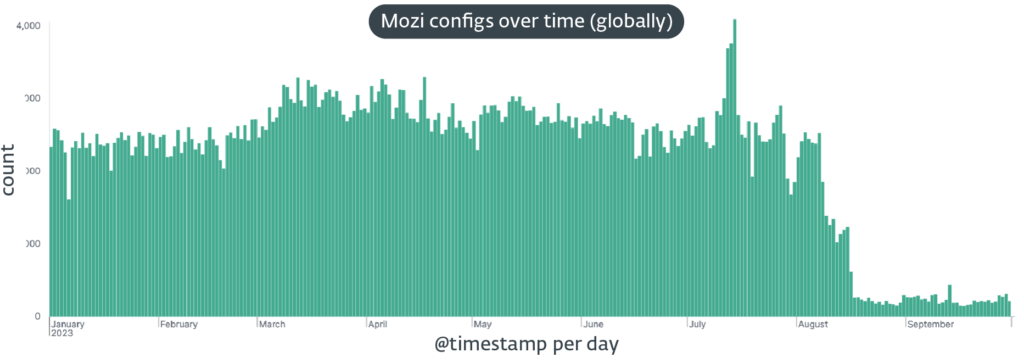
The recent shutdown of the Mozi botnet is believed to be the work of its operators, who may have been forced to kill their creation by Chinese authorities. This is a theory from cybersecurity firm ESET, whose researchers recently discovered a kill switch suggesting that the takedown was deliberate. Mozi emerged in September 2019 and […]
Budget Cuts at CISA Could Affect Enterprise Cybersecurity
The US Cybersecurity and Infrastructure Security Agency’s efforts to combat disinformation about US elections and election infrastructure — a tiny part of its overall mission — may lead to budget cuts that affect CISA’s two principal responsibilities: defending federal networks and aiding critical infrastructure operators against cyberattackers. Last month, half of House Republicans voted for […]