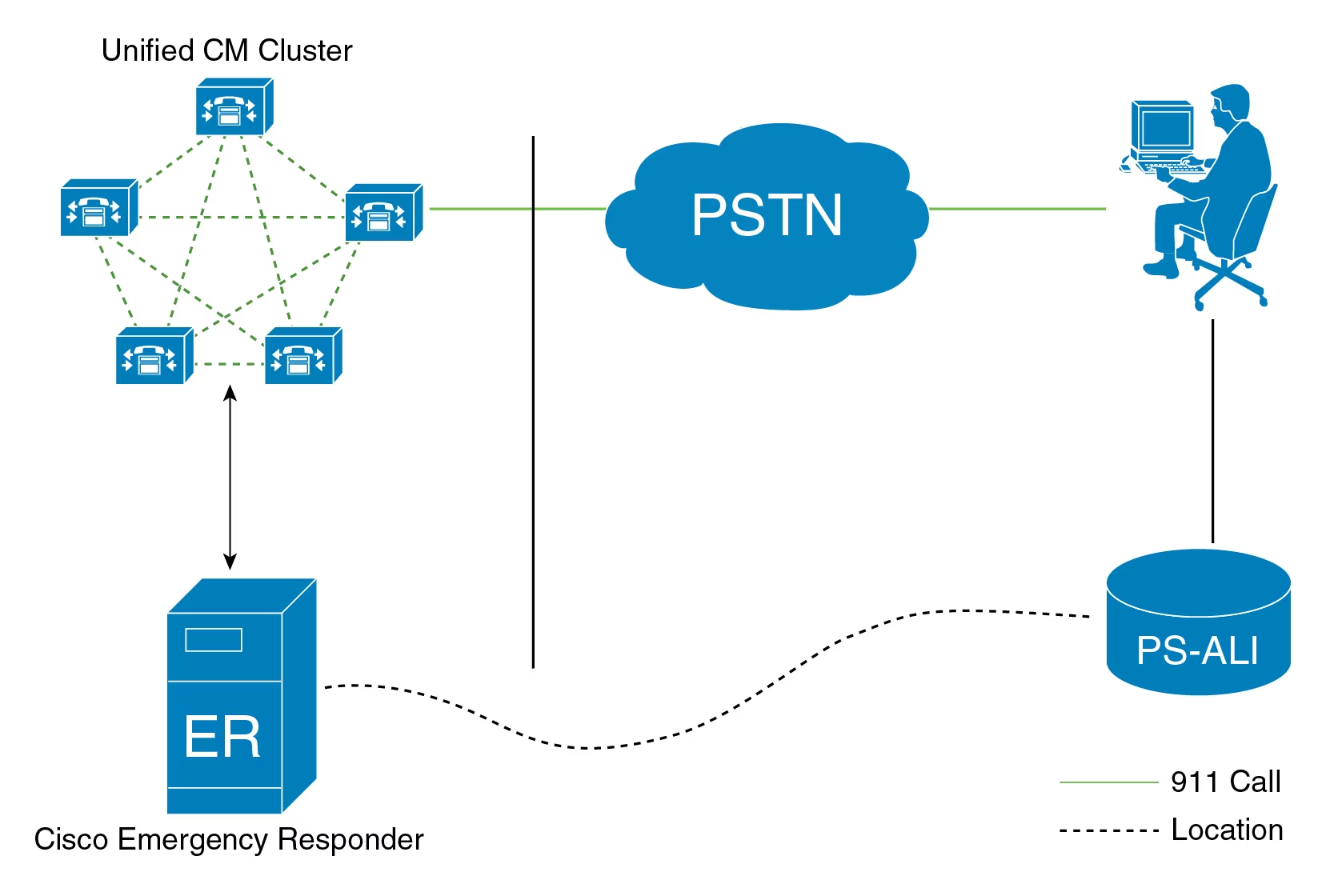
A remotely exploitable vulnerability in the Cisco Emergency Responder software could allow an unauthenticated attacker to log in to an affected device using the root account, according to a warning from the U.S. tech vendor. The vulnerability, tracked as CVE-2023-20101, carries a CVSS severity score of 9.8/10 and a “critical” tag from Cisco’s security response […]
Update on Naked Security – Sophos News
Dear Naked Security readers, Firstly, thank you for your interest, your time, and your contributions to the Naked Security community. Your invaluable engagement and expertise have helped improve cybersecurity for everyone. We have recently added the extensive catalog of Naked Security articles to the Sophos News blog platform, enabling us to provide all Sophos security […]