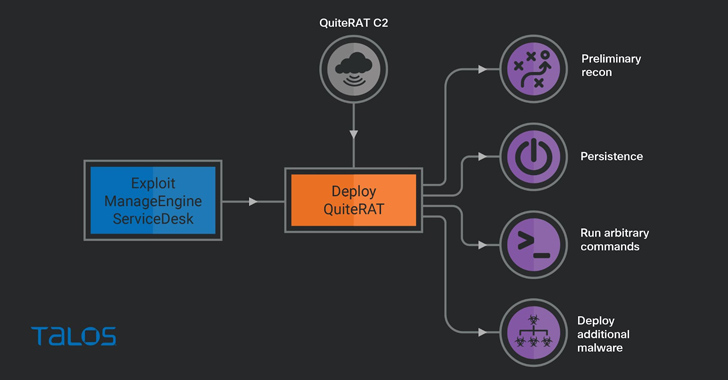
Financial services companies breached as a result of MOVEit zero-day vulnerability are facing a flurry of class action lawsuits over the exposure of sensitive customer financial data. TD Ameritrade and Charles Schwab are the latest firms facing suits, this time in the US District Court in Nebraska by David Schultz, who on Aug. 23, filed […]
Chris’ Corner: Even More SVG Tricks
SVG has so many tricks up its sleeve. It’s really a full-featured drawing API literally designed for the web, but few of us really truly understand it nor reach for it enough. Heck, I even wrote a book about it, and I don’t. At the time, just getting people to use SVG for icons felt […]