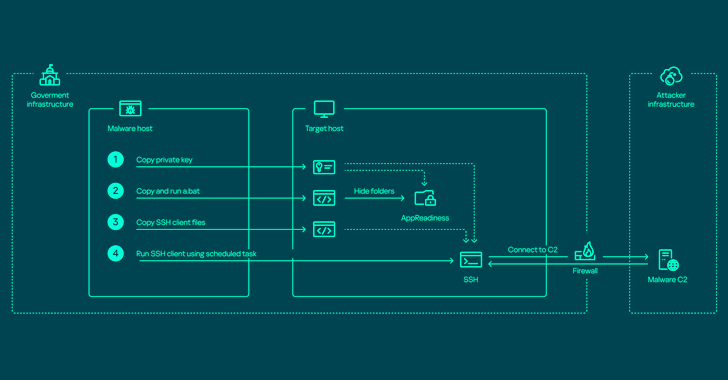
In the wake of a cyberattack that led to operational troubles, the city council for Leicester City, England, is still struggling with its city’s streetlights failing to shut off. Roger Ewens, a resident of Beaumont Leys, was among those who noticed the streetlights in Leicester were on day and night. “I noticed that down Anstey […]
Apple Vision Pro FAQ: Price, features, hands-on insights, and everything you need to know
Jason Hiner/ZDNET An Apple AR/VR headset — rumored for more than six years — finally became available this year. Eight months after Apple announced the Vision Pro at WWDC, the headset began shipping to customers. The highly anticipated headset was designed to take mixed-reality experiences to the next level. Apple has even claimed the Vision […]