Recent headlines have cast a spotlight on the evolving nature of cyber threats and their ripple effects across industries, accentuating the value of sensitive information in the modern threat landscape. The seismic SolarWinds attack, a supply-chain breach with widespread ramifications, underscores the transformation in hackers’ motivations — transitioning from a singular pursuit of financial gain to […]
New Advanced Backdoor with Distinctive Malware Tactics
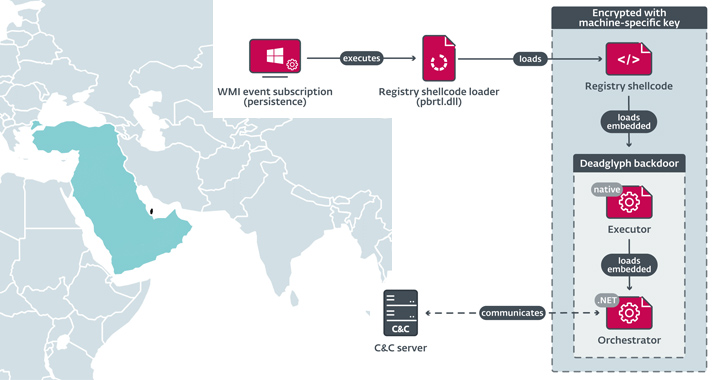
Sep 23, 2023THNCyber Espionage / Malware Cybersecurity researchers have discovered a previously undocumented advanced backdoor dubbed Deadglyph employed by a threat actor known as Stealth Falcon as part of a cyber espionage campaign. “Deadglyph’s architecture is unusual as it consists of cooperating components – one a native x64 binary, the other a .NET assembly,” ESET […]