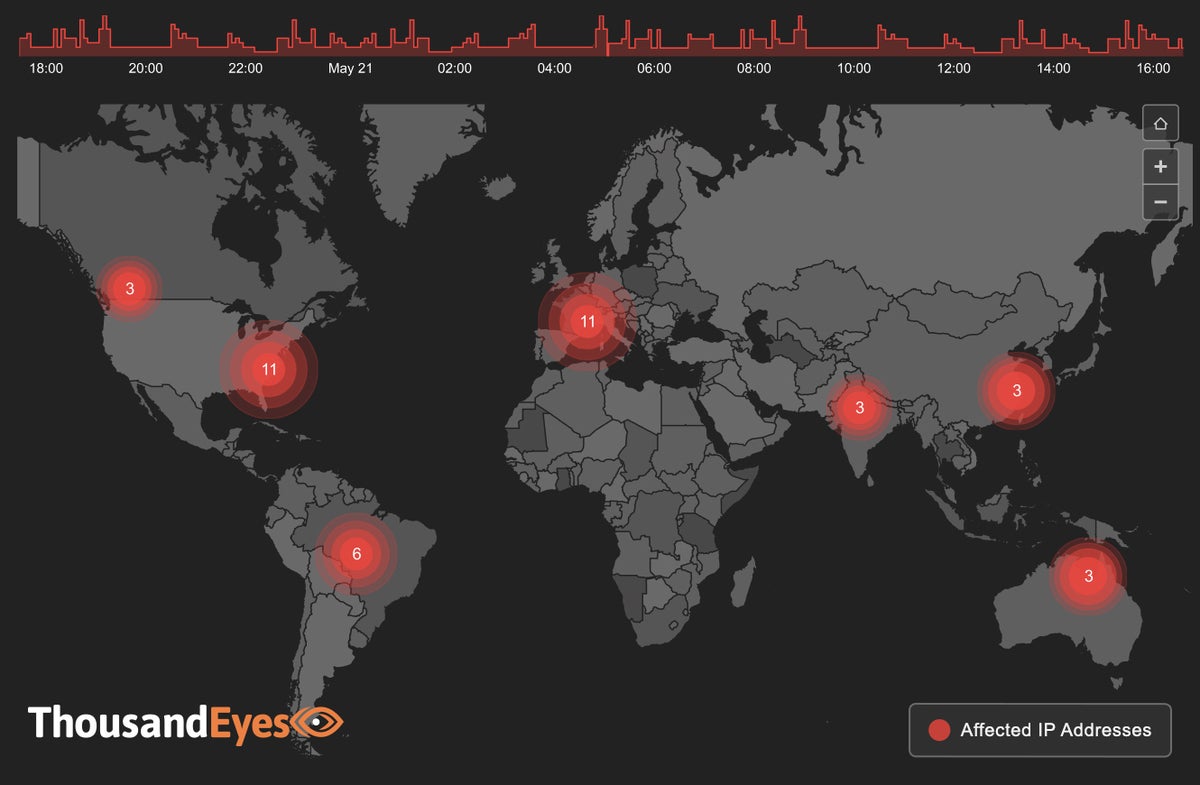
The reliability of services delivered by ISPs, cloud providers and conferencing services (a.k.a. unified communications-as-a-service (UCaaS)) is an indication of how well served businesses are via the internet. ThousandEyes is monitoring how these providers are handling the performance challenges they face. It will provide Network World a roundup of interesting events of the week in […]
Dart Extensions Tutorial: Improve your Flutter Code
Learn how to take your Flutter skills to the next level and make your code reusable with one of Dart’s most useful features: Dart extensions. You might already have become familiar with basic Flutter and Dart knowledge. You might even have your first app already published. Yet there is always room for improvement. Dart Extensions […]