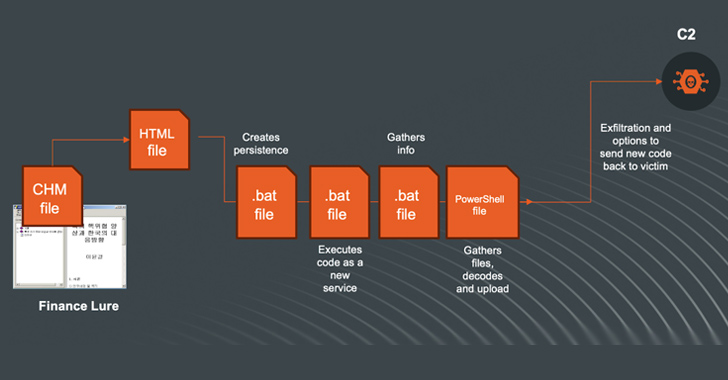
The North Korea-linked threat actor known as Kimsuky (aka Black Banshee, Emerald Sleet, or Springtail) has been observed shifting its tactics, leveraging Compiled HTML Help (CHM) files as vectors to deliver malware for harvesting sensitive data. Kimsuky, active since at least 2012, is known to target entities located in South Korea as well as North America, Asia, […]
US organizations targeted with emails delivering NetSupport RAT
Employees at US-based organizations are being targeted with emails delivering NetSupport RAT malware via “nuanced” exploitation and by using an advanced detection evasion method. The malware campaign The campaign, dubbed PhantomBlu, takes the form of email messages purportedly coming from a legitimate accounting service. The attackers are leveraging a legitimate email delivery platform, “SendInBlue” or […]