
The business reality of AI for cybersecurity – Sophos News
[ad_1] AI is firmly embedded in cybersecurity. Attend any cybersecurity conference, event, or trade show and AI is invariably the single biggest capability focus. Cybersecurity

[ad_1] AI is firmly embedded in cybersecurity. Attend any cybersecurity conference, event, or trade show and AI is invariably the single biggest capability focus. Cybersecurity

[ad_1] COMMENTARY Cyber threats have never held greater risk to digital business operations than they do today. At Natco Home Group, we received a wake-up

[ad_1] A high-severity security flaw has been disclosed in Meta’s Llama large language model (LLM) framework that, if successfully exploited, could allow an attacker to

[ad_1] The FBI is on a mission to raise awareness about the threat that North Korean IT workers present to organizations in the US and

[ad_1] NEWS BRIEF Cyberattackers are using a new threat vector involving several Ivanti vulnerabilities in order to subvert the company’s Cloud Service Appliance (CSA). According
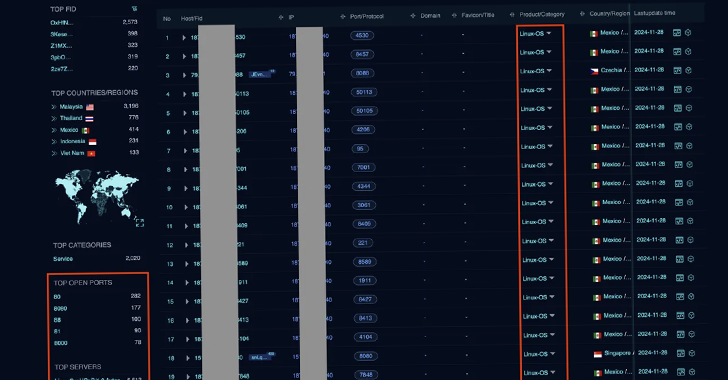
[ad_1] Jan 21, 2025Ravie LakshmananBotnet / Vulnerability Cybersecurity researchers have warned of a new large-scale campaign that exploits security flaws in AVTECH IP cameras and

[ad_1] Sophos X-Ops’ Managed Detection and Response (MDR) is actively responding to incidents tied to two separate groups of threat actors, each of which have

[ad_1] Business Security Data breaches can cause a loss of revenue and market value as a result of diminished customer trust and reputational damage 21

[ad_1] Resecurity, a global leader in cybersecurity solutions, unveiled its advanced Government Security Operations Center (GSOC) during NATO Edge 2024, the NATO Communications and Information

[ad_1] Japanese device maker I-O Data this week confirmed zero-day exploitation of critical flaws in multiple routers and warned that full patches won’t be available
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
We Schedule a call at your convenience
We do a discovery and consulting meting
We prepare a proposal