In the VLAN Access-List (VACL) lesson, we looked at how VACLs can filter L2 items such as EtherTypes or MAC addresses. What surprises many network engineers though, is that MAC access-lists only apply to non-IPv4 traffic. Even if you create a filter for a MAC address and deny it, the traffic will be permitted if the Ethernet frame carries an IP packet. To demonstrate this, we’ll look at two different scenarios where we try to filter something and see if the switch ignores the traffic or not.
Configuration
Here is the topology:
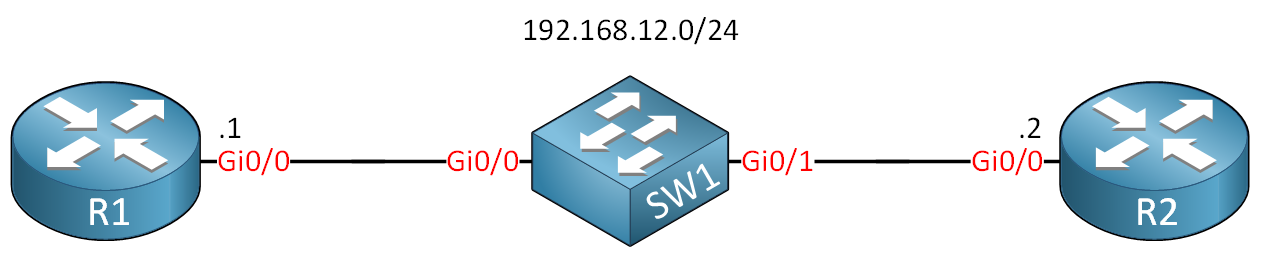
We only need two routers and a switch:
- Switch: WS-c3650-24PDM running Cisco IOS XE Software, Version 16.12.08.
- Routers: ISR 4331 routers running Cisco IOS Software, ISR Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 15.5(2)S3, RELEASE SOFTWARE (fc2).
We’ll use the routers to generate traffic and the switch to configure a VACL.
PPPoE
To test if the VACL filters on L2, we’ll use an L2 protocol that works end-to-end between R1 and R2. I’ll use PPPoE for this. R1 is the server, and R2 is the client.
You can see what the PPPoE packets look like here:
Configurations
Want to take a look for yourself? Here ,you will find the startup configuration of each device.
R1
hostname R1
!
bba-group pppoe global
virtual-template 1
!
interface GigabitEthernet0/0/0
mac-address 0000.5e00.5301
no ip address
negotiation auto
pppoe enable group global
!
interface Virtual-Template1
mtu 1492
ip address 192.168.12.1 255.255.255.0
peer default ip address pool CLIENT
ppp authentication chap callin
!
ip local pool CLIENT 192.168.12.2
!
endR2
hostname R2
!
interface GigabitEthernet0/0/0
mac-address 0000.5e00.5302
no ip address
pppoe enable group global
pppoe-client dial-pool-number 1
!
interface Dialer1
ip address negotiated
encapsulation ppp
dialer pool 1
ppp chap hostname R2
ppp chap password 0 CISCO
!
endSW1
hostname SW1
!
interface GigabitEthernet1/0/1
switchport access vlan 12
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/2
switchport access vlan 12
switchport mode access
spanning-tree portfast
!
endLet’s check if the PPPoE session works:
R1#show pppoe session
1 session in LOCALLY_TERMINATED (PTA) State
1 session total
Uniq ID PPPoE RemMAC Port VT VA State
SID LocMAC VA-st Type
1 1 0000.5e00.5302 Gi0/0/0 1 Vi2.1 PTA
0000.5e00.5301 UPR2#show pppoe session
1 client session
Uniq ID PPPoE RemMAC Port VT VA State
SID LocMAC VA-st Type
N/A 1 0000.5e00.5301 Gi0/0/0 Di1 Vi2 UP
0000.5e00.5302 UPThat seems to be the case. Let’s try a ping:
R1#ping 192.168.12.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 msThis works. Now, let’s see if we can filter this traffic. Here is the MAC address of R2:
R2#show interfaces GigabitEthernet 0/0/0 | include address
Hardware is ISR4331-3x1GE, address is 0000.5e00.5302 (bia cc8e.710c.d9b0)Let’s create a MAC access-list that filters the MAC address of R2 when it’s the source address:
SW1(config)#mac access-list extended R2_MAC
SW1(config-ext-macl)#permit any host 0000.5e00.5302We’ll create a VACL:
SW1(config)#vlan access-map BLOCK_R2 10
SW1(config-access-map)#match mac address R2_MAC
SW1(config-access-map)#action drop
SW1(config-access-map)#exit
SW1(config)#vlan access-map BLOCK_R2 20
SW1(config-access-map)#action forwardThis VACL denies source MAC address 0000.5e00.5302 and permits everything else. Let’s activate if for VLAN 12:
SW1(config)#vlan filter BLOCK_R2 vlan-list 12That’s it. Let’s try another ping:
R1#ping 192.168.12.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)The ping fails. This proves that our VACL works. Unfortunately, my switch doesn’t show any hits:
SW1#show access-lists R2_MAC
Extended MAC access list R2_MAC
permit any host 0000.5e00.5302
SW1#show vlan access-map BLOCK_R2
Vlan access-map "BLOCK_R2" 10
Match clauses:
mac address: R2_MAC
Action:
drop
Vlan access-map "BLOCK_R2" 20
Match clauses:
Action:
forwardSW1#show vlan filter
VLAN Map BLOCK_R2 is filtering VLANs:
12The ping that fails is sufficient, though.
IPv4
Now, let’s try something else. We’ll use regular IP packets encapsulated in Ethernet frames this time. Let’s get rid of PPPoE first and switch to IP.
Configurations
Want to take a look for yourself? Here, you will find the startup configuration of each device.
R1
hostname R1
!
interface GigabitEthernet0/0/0
mac-address 0000.5e00.5301
ip address 192.168.12.1 255.255.255.0
!
endR2
hostname R2
!
interface GigabitEthernet0/0/0
mac-address 0000.5e00.5302
ip address 192.168.12.2 255.255.255.0
!
endSW1
hostname SW1
!
interface GigabitEthernet1/0/1
switchport access vlan 12
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/2
switchport access vlan 12
switchport mode access
spanning-tree portfast
!
endThe first time you try to send a ping with the VACL active, it will fail. That’s not because the VACL filters the IP address but because it blocks the ARP packets. Without ARP, the hosts are unable to reach each other.
To work around this issue, we’ll use two static ARP entries:
R1(config)#arp 192.168.12.2 0000.5e00.5302 ARPAR2(config)#arp 192.168.12.1 0000.5e00.5301 ARPAThe VACL is still active:
SW1#show vlan filter
VLAN Map BLOCK_R2 is filtering VLANs:
12Let’s try a ping:
R1#ping 192.168.12.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.12.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 msThis ping works and proves that VACLs ignore Ethernet frames carrying IP packets, even though this traffic matches our access-list.
ipv6 same thing.
Conclusion
You have now seen that VACLs ignore IP packets even though the access-list matches a MAC address that should be dropped. If you want to filter IP packets, you should use IP access lists. I hope you enjoyed this lesson. If you have any questions, feel free to leave a comment!
[ad_2]
Source link



