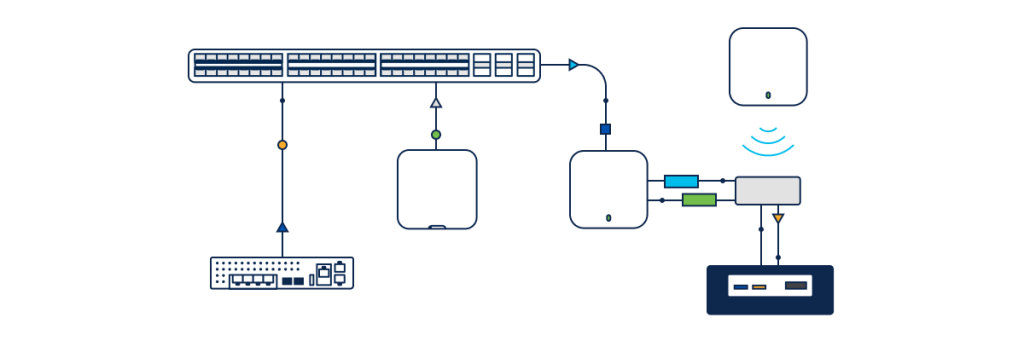
Wi-Fi 7 multi-link operation (MLO) explained
[ad_1] There’s a great deal of talk around the capability of Wi-Fi 7 (IEEE 802.11be) to revolutionize the wireless experience. It’s not hype. A key

[ad_1] There’s a great deal of talk around the capability of Wi-Fi 7 (IEEE 802.11be) to revolutionize the wireless experience. It’s not hype. A key

[ad_1] The issue doesn’t affect the company’s Cloud NGFW or Prisma Access software. Greynoise said exploitation began around Tuesday of this week. Assetnote published research

[ad_1] Companies are deploying identity and access management (IAM) at a record pace as they seek ways to harden their network security. According to market

[ad_1] Enterprises are ramping up AI deployments throughout their operations. Generative AI (GenAI) tool adoption alone has significantly increased in the past year. According to

[ad_1] Essentials is geared toward data center network engineers, data center system engineers, IT infrastructure architects, and IT operations engineers. The training focuses on professionals

[ad_1] When I talk to customers, I often hear that their workplaces are not ready to handle the competing demands created by distributed work and

[ad_1] AI data centers must support much higher power densities than traditional data centers: Nvidia’s GB200 NVL72 systems are estimated to consume up to 120kW

[ad_1] After a year peppered with news about subsea cable cuts, Amazon, Meta and Google are planning new cabling systems for 2025, spending big to

[ad_1] In January 2025, Cisco held its inaugural AI Summit in Silicon Valley, where tech leaders discussed the opportunities and ethics around AI. The event

[ad_1] Digital transformation has redefined how enterprises do business, as they search for ways to improve operations and better serve their customers. Organizations have modernized
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
We Schedule a call at your convenience
We do a discovery and consulting meting
We prepare a proposal