There are more vulnerabilities around than ever. The Verizon Data Breach Investigations Report highlighted an almost 200% growth in the exploitation of vulnerabilities in 2023. In the first seven months of 2024, new vulnerabilities rose by another 30% compared to the previous year. No wonder vulnerability management tools are becoming a staple of the enterprise cybersecurity arsenal.
“Vulnerability management is a core function of cybersecurity,” said Michelle Abraham, research director, Security and Trust at IDC. “Leaving vulnerabilities without action exposes organizations to endless risk since vulnerabilities may leave the news but not the minds of attackers.”
Top vulnerability management tools comparison
Many vulnerability management tools have similar features. But when I looked into them more closely, I noticed that they each have their own focus or approach. Some are more specialized than others. I compared them based on price as well as four key features:
- Cloud, on-prem, or both.
- Being part of a comprehensive cybersecurity suite.
- Automated discovery.
- Automated remediation.
Be aware, however, that an apples-to-apples comparison based on price is impossible due to the different ways vendors price their products and services as well as a lack of transparency on pricing.
| Starting price | Cloud or on-prem | Cybersecurity suite features | Automated discovery | Automated remediation | |
|---|---|---|---|---|---|
| Tenable | About $4,000 per year for 100 assets. | Cloud-based. There is a separate on-prem suite called Tenable Security Center that includes vulnerability management. | Vulnerability management, web application scanning, cloud security, identity exposure, operational technology security, attach surface management, and risk assessment. | Yes | Yes |
| ESET | $275 for five devices per year for the ESET Protect package that includes ESET Vulnerability and Patch Management | Cloud-based. A separate on-prem suite is available that includes vulnerability management | EDR, server security, mobile threat defense, encryption, threat defense, cloud protection, vulnerability & patch management, MFA, and MDR | Some automated discovery but not as broad as some of the others | Some auto-remediation capabilities are included |
| Syxsense | $9 per device per month or $960 per year for 10 devices | One version for the cloud and another for on prem | Patch management, vulnerability scanning, IT management, mobile device management, and zero trust | Yes | Yes |
| CrowdStrike | $184 per year for the full suite and about $40 per year for Exposure Management | Cloud-based | EDR, antivirus, threat hunting/intelligence, exposure management, AI, threat hunting, cloud security, SIEM, data protection, automation | Yes | Yes |
| Qualys | $295 per year for the small business version and about $2000 for the enterprise version. | Cloud-based with an on-prem version available. | Asset management, vulnerability & configuration management, risk remediation, threat detection & response, EDR, cloud security, and compliance. | Yes | Yes |
| Rapid7 | $6 per month per asset or $2 per month per asset for a 500-asset license. | Cloud and on-prem | AI engine, XDR, exposure management, and attack surface management. | Yes | Yes |
| Ivanti | $4 per month per user. | Cloud or on-prem | Discovery, IT automation, real-time insight, endpoint management, network and endpoint security, supply chain, and service and asset management. | Yes | Yes |
| StorageGuard | $200 per month for up to 50 systems. | Cloud | No | Yes | Limited |
Tenable Vulnerability Management: Best overall

Tenable Vulnerability Management takes a risk-based approach to vulnerability management. It focuses on network visibility in order to predict when attacks will occur and to be able to respond rapidly when critical vulnerabilities are in play. A 60-day free trial is available.
SEE: How to Create an Effective Cybersecurity Awareness Program (TechRepublic Premium)
Why I chose Tenable
I selected Tenable as the best overall vulnerability management tool overall for many reasons. It is the market leader among vulnerability management tools with a 25% market share. It includes a wealth of features and ticks just about all the boxes. It contains hundreds of integrations with other platforms and security tools that make automation of workflows easy and reduce the number of resources needed to keep the enterprise safe.
Pricing
- Tenable costs about $4,000 per year for 100 assets.
Features
- The Tenable Community is active with plenty of users willing to assist you to address problems.
- Active and passive scanning of on-premise systems, virtual machines, cloud instances, and mobile devices.
- Cloud Connectors give continuous visibility and assessment into public cloud environments like Microsoft Azure, Google Cloud Platform, and Amazon Web Services.
- Built-in prioritization, threat intelligence, and real-time reporting help users to understand risk and proactively disrupt attack paths.
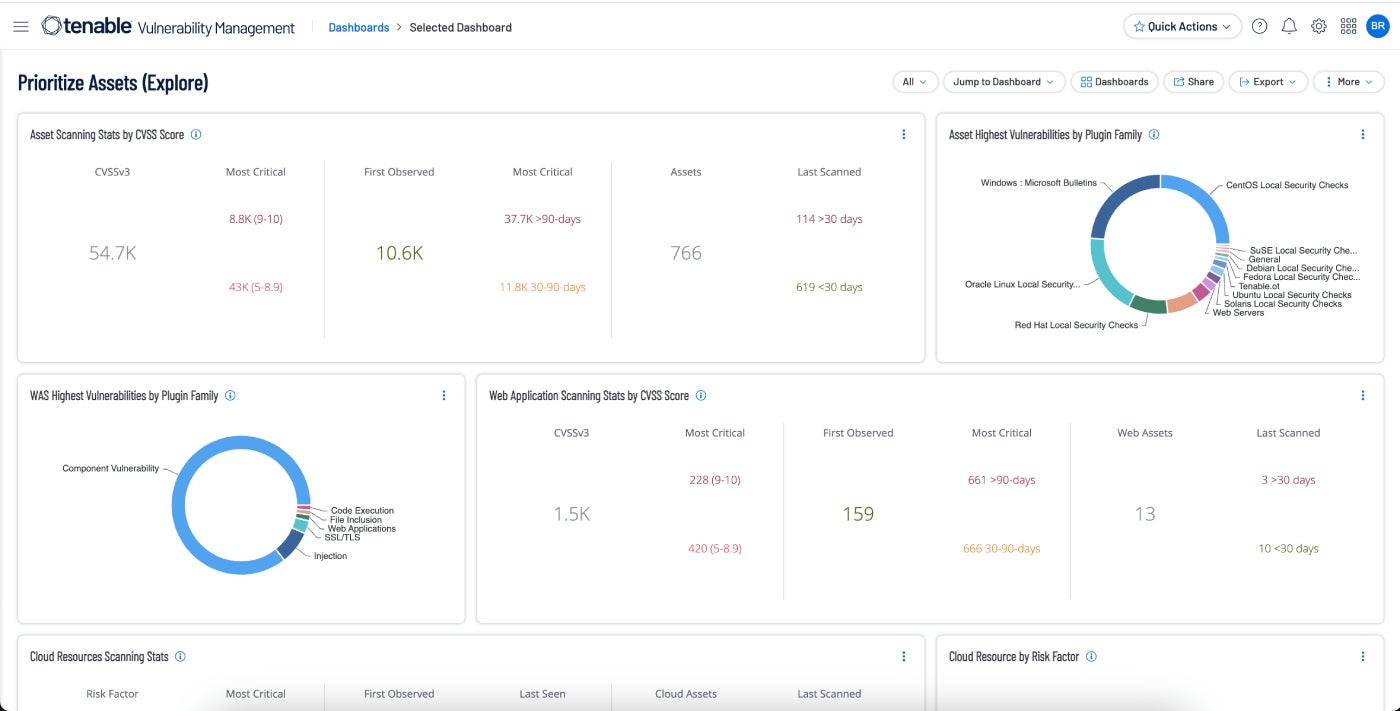
Pros and cons
| Pros | Cons |
|---|---|
| Fully integrated into the broader Tenable One platform. | Some users report that support could be improved. |
| Continuous, always-on discovery and assessment | Real-time scanning and overall scanning speed could be improved. |
| Threat intelligence | Not the cheapest solution on the market. |
| Automated vulnerability prioritization. | Better suited to experienced IT professionals |
| Real-time visualization of risk, and tracking of vulnerabilities, assets, and remediations. | |
| Vulnerability risk scores to identify risk. |
ESET Vulnerability and Patch Management: Best for SMEs

ESET Vulnerability and Patch Management can automatically scan thousands of applications for any of tens of thousands of common vulnerabilities and exposures. It can prioritize and filter vulnerabilities by exposure score and severity.
Why I chose ESET Vulnerability and Patch Management
I liked ESET as it is easy to install and run. This makes it attractive for SMEs and larger organizations that lack IT and cybersecurity resources.
Pricing
- $275 for five devices per year for the ESET Protect package that includes ESET Vulnerability and Patch Management.
Features
- Supports multiple versions of Windows, Linux, and macOS.
- Detects over 35,000 CVEs.
- Automated scans with customizable schedule settings.
- Prioritizes and filters vulnerabilities by exposure score and severity.
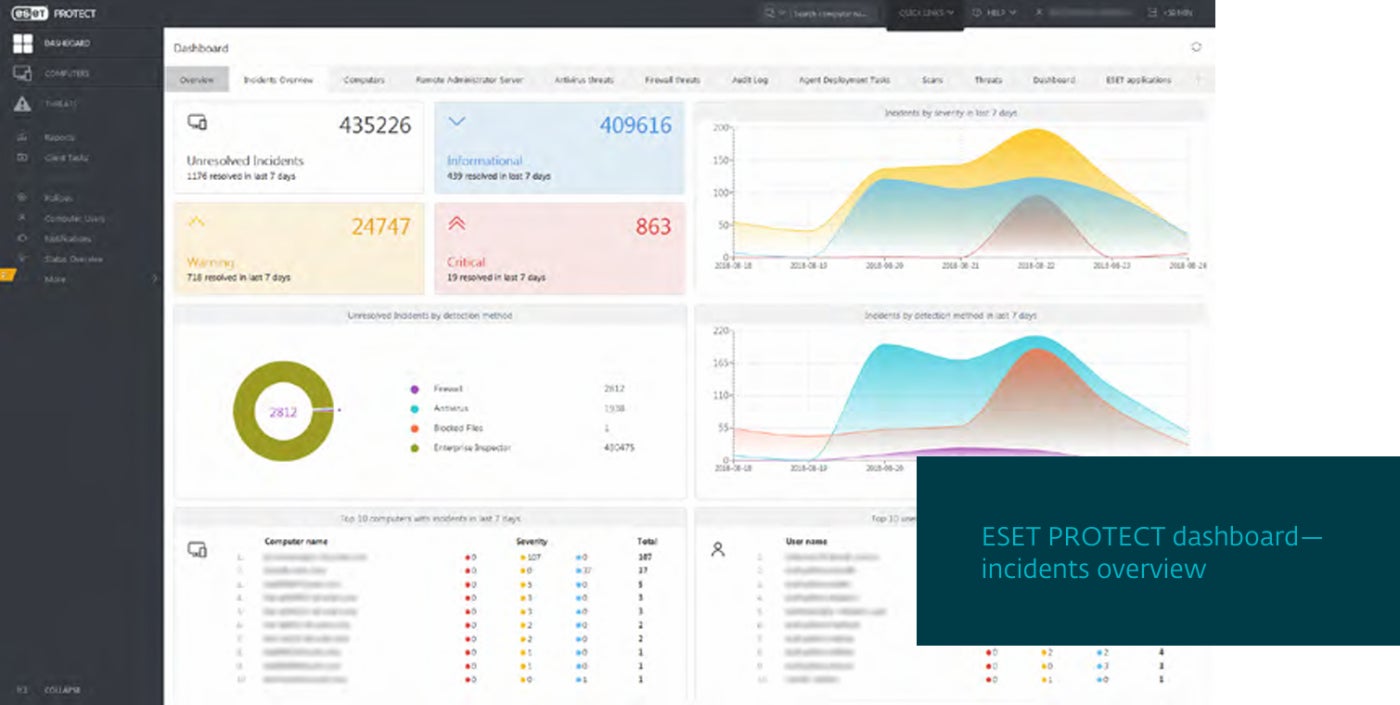
Pros and cons
| Pros | Cons |
|---|---|
| Simplifies patching by prioritizing critical assets and scheduling the remainder for off-peak times. | Automated discovery and remediation features lack the scope of some other solutions. |
| Protection against ransomware and zero-day threats. | More focused on small and mid-size organizations rather than the enterprise market. |
| Easy to set up, use, and maintain. |
Syxsense Enterprise: Best for patch management

Syxsense Enterprise includes patch management, vulnerability scanning, IT management, and mobile device management within its vulnerability management platform. Most recently, it has added integrated remediation features as well as zero trust. Everything is now combined into one console via Syxsense Enterprise.
Why I chose Syxsense
Syxsense began life as a patch management specialist. Building on that success, it has steadily expanded into a full featured vulnerability management suite. However, I noticed that it doesn’t encompass the breadth of security modules that many of the other vendors in this guide. It is missing SIEM, threat intelligence, and antivirus, for example. Despite that, I liked the tight focus on vulnerability and device management. For those that already have a security platform and just want to improve patch management and vulnerability management, Syxsense is a good choice.
Pricing
- $9 per device per month or $960 per year for 10 devices.
Features
- Automated discovery and remediation workflows.
- Comprehensive patch management including patch supersedence, patch rollback, and patching any endpoint including mobile devices.
- A Zero Trust Evaluation Engine creates a trusted security posture for endpoints.
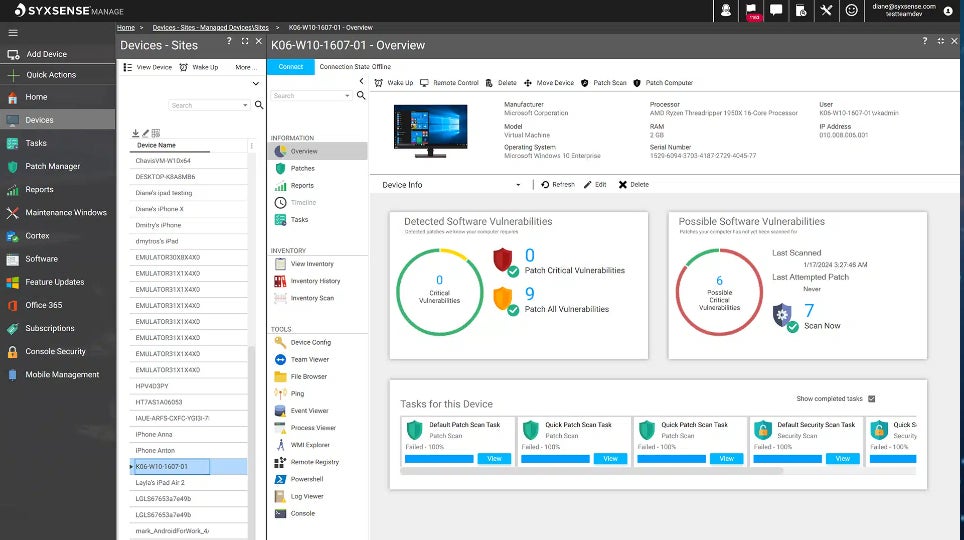
Pros and cons
| Pros | Cons |
|---|---|
| Excellent patch management functionality. | Syxsense was just acquired by Absolute Security, which could impede the high level of continuous innovation that propelled Syxsense to the forefront of the patch and vulnerability management field. |
| Tightly focused on vulnerability management. | Suite is missing elements such as antivirus, threat hunting, and SIEM. |
| Separate versions for cloud and on-prem. |
CrowdStrike Exposure Management: Best cybersecurity suite incorporating vulnerability management

CrowdStrike Exposure Management grew out of an older product known as Falcon Spotlight, which I was already familiar with. I noticed how it broadens the capabilities of Falcon Spotlight by adding more of a risk management approach along with a host of AI-based capabilities.
Why I chose CrowdStrike Exposure Management
CrowdStrike Exposure Management is a solid product in its own right. It is one part of a comprehensive suite with a wide range of security features. Most buyers will purchase the complete CrowdStrike platform rather than only the Exposure Management element. Known as the CrowdStrike Falcon Platform, it encompasses EDR, antivirus, threat hunting/intelligence, exposure management, AI, threat hunting, cloud security, SIEM, data protection, automation, and more, all from a single agent. Anyone needing a vulnerability management tool and a new security suite can’t go far wrong adopting the entire Falcon Platform.
Pricing
- $184 per year for the full suite and about $40 per year for the exposure management module.
Features
- Automated assessment for vulnerabilities, whether on or off the network.
- Shortened time-to-respond with real-time visibility into vulnerabilities and threats.
- The ability to prioritize and predict which vulnerabilities are most likely to affect the organization.
- The company boasts a single lightweight-agent architecture.
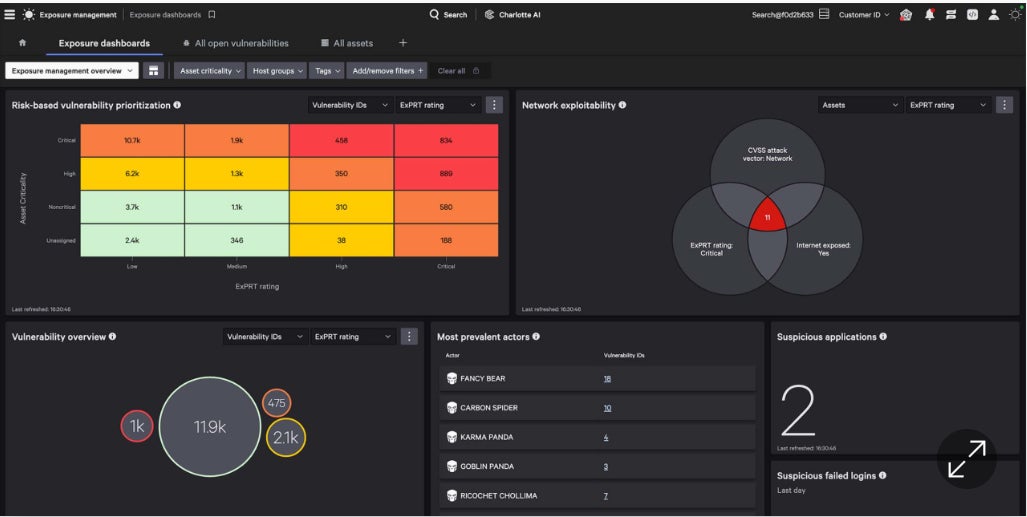
Pros and cons
| Pros | Cons |
|---|---|
| Vulnerability and patching orchestration. | Limited capabilities when it comes to scanning for misconfigurations in security applications. |
| Integration within the CrowdStrike Falcon. | More focus on the entire suite than on vulnerability management. |
| AI ties together threat intelligence with vulnerability assessment in real time. | |
| A single agent for all modules. |
Qualys VMDR: Best for cloud-based enterprises

Qualys Vulnerability Management Detection and Response takes the context of threats into account as a way to prioritize and remediate serious threats rapidly. I appreciated the value of its automated scoring methodology, known as TruRisk.
Why I chose Qualys VMDR
Qualys VMDR does a good job bringing together a set of key security functions, including vulnerability assessment, asset discovery, inventory management, and attack surface management. It is part of a large, cloud-based suite of security products. As such, I consider it to be a good choice for enterprises and larger businesses operating in the cloud.
Pricing
- Qualys pricing seemed quite complex to me. It is based on the number or compute units in the cloud: virtual machines, serverless, and container images. The unit value varies based on differences in the functionality, complexity, and overall value proposition of each module. The enterprise version of the entire suite starts at about $500 per month and ramps up from there based on the number of users. The vulnerability management module is said to be available to small businesses starting at $250 per year and $2000 for enterprises.
Features
- Primarily cloud-based but an on-prem private cloud appliance is available for customers with strict data sovereignty requirements.
- A cloud-based service offered primarily to SMEs provides VMDR along with endpoint detection and response and patch management tools.
- Risk-based and context-based prioritization of threats
- Integration with patch management, inventory management, and ITSM.
- Qualys Threat Research Unit proactively searches for new threats by analyzing data from its user base, dozens of threat intelligence feeds, third-party data, and the dark web.
Pros and cons
| Pros | Cons |
|---|---|
| Broad range of vulnerability signature databases. | Can be challenging to install, learn, and use for less mature IT shops. |
| Real-time detection of vulnerabilities such as patches that need to be installed and misconfigurations. | Cloud and hypervisor support could be improved. |
| Automatically detects the latest superseding patch for the vulnerable asset and deploys it. | |
| Qualys is one of the market leaders in vulnerability management based on market share. |
Features
- Continually assesses and prioritizes critical vulnerabilities using risk scoring from 1 to 1000.
- Tracks compliance against policy and regulations, and compares to industry benchmarks.
- Rapid7 Labs helps identify all internet-facing assets and alert on vulnerabilities.
- Good scanning consistency and range of devices.
Pros and cons
| Pros | Cons |
|---|---|
| Automated remediation. | Best suited to knowledgeable security teams. |
| Automatic pen-testing. | Can sometimes be complicated to set up. |
| One of the top vulnerability management vendors per market share. | Some users note integration and deployment issues |
| Runs vulnerability scans across cloud, physical, and virtual infrastructure and automatically collects data from all endpoints. | Support responsiveness could be improved. |
| Security teams can streamline remediation activities such as vulnerability patching and containment. | |
| Integrates with a range of third-party tools including ticketing systems, patch management solutions, and SIEM. |
Ivanti VMaaS: Best as a service offering

Ivanti has a long history as a top vulnerability management vendor. It offers tools you can deploy within the enterprise or as a service.
Why I chose Ivanti VMaaS
For me, Ivanti VMaaS stands out due to its pairing of vulnerability management as-a-service with expert security analysts, scanning tools, and processes that help businesses identify vulnerabilities on the network and in applications. But the company also offers top cloud-based tools such as Ivanti Neurons for risk-based vulnerability management.
Pricing
Features
- Ivanti Neurons for RBVM, can ingest data from multiple third-party scanners to help close gaps and blind spots.
- It automatically analyzes data from vulnerability scanners and provides insight to IT and security teams.
- Scan findings are automatically correlated and contextualized with threat data and analysis, and prioritized.
- Finds code weakness and pinpoints coding errors.
Pros and cons
| Pros | Cons |
|---|---|
| This fully managed service frees up personnel for other projects. | Some users complain of lack of support. |
| Easy-to-follow remediation plans. | Customization options are limited. |
| Risk scoring ensures remediation recommendations are focused on actions that target the most serious threats. | Competitive patch management products may be more comprehensive at discovering all endpoints operating on the network. |
| Automated workflows. |
StorageGuard: Best for storage and backup applications

StorageGuard by Continuity Software scans, detects, and fixes security misconfigurations and vulnerabilities across hundreds of storage, backup, and data protection systems.
Why I chose StorageGuard
Most tools in this guide provide broad coverage — either across the entire vulnerability management landscape or are part of large security suites that go far beyond vulnerability management. I picked StorageGuard as it takes the opposite approach. It is laser-focused on one aspect of this market: a comprehensive address to a major gap found in many vulnerability management products — storage and backup vulnerabilities and misconfigurations. StorageGuard fills that niche so well that I recommend its use in conjunction with some of the other tools listed here.
Pricing
- $200 per month for up to 50 systems.
Features
- Directly addresses the vulnerabilities and potential threats listed by NIST in Security Guidelines for Storage Infrastructure.
- Broad coverage of storage and backup apps and systems from the likes of Dell, NetApp, Hitachi Vantara, Pure, Rubrik, Commvault, Veritas, HPE, Brocade, Cisco, Veeam, Cohesity, IBM, Infinidat, VMware, AWS, and Azure.
- Can detect deviation from a chosen configuration baseline.
Pros and cons
| Pros | Cons |
|---|---|
| Scans and finds weaknesses in storage and backup applications that other scanners miss. | Does not address traditional vulnerabilities in third party applications and OSes. |
| Users comment on ease of use and thoroughness in finding backup and storage misconfigurations. | Focused mainly on discovery of issues as opposed to resolution. |
| Provides proof of audit compliance against CIS Controls, NIST, ISO, PCI, NERC CIP, and others. |
Vulnerability management: Frequently asked questions
What are vulnerability management tools?
According to NIST, vulnerability management is a “capability that identifies vulnerabilities [common vulnerabilities and exposures] on devices that are likely to be used by attackers to compromise a device and use it as a platform from which to extend compromise to the network.”
As well as mitigating configuration or code issues that might allow an attacker to exploit an environment, the definition is often broadened to include patch management, MDM, IT asset management, and EDR. The vulnerability management function is often integrated into a large security suite.
How do vulnerability management tools work?
Vulnerability management can be broken into a series of steps, many of which are now automated:
- Vulnerability scanning.
- Reporting on any vulnerabilities discovered and prioritization based on their potential impact on the business.
- Deployment of remediation or recommendation of remediation steps.
- Validation of remediations to ensure issues have been resolved.
- Reporting on the state of vulnerabilities and their resolution within the enterprise.
How are vulnerability management tools deployed?
They can be deployed as on-premises software, delivered as SaaS, or as managed services.
What is vulnerability management as a service?
Vulnerability management as a managed service is delivered by a provider via the cloud rather than downloading and running on-prem software. It continuously identifies, assesses, reports, and manages vulnerabilities across cloud identities, workloads, platform configurations, and infrastructure.
What features should I look for in a top vulnerability management tool?
Certain core functions are present in all top vulnerability management platforms. These include:
- Discovery of all devices, applications, and systems and detection of potential vulnerabilities and misconfigurations that may exist anywhere within the network on any device that connects to the network.
- A database of vulnerabilities and threats that is continuously updated.
- Integration with a wide range of platforms, security systems, vulnerability scanners, ticketing systems, and other security tools.
- A method of risk scoring and prioritization.
- Automatic remediation or remediation guidance.
- Reporting capabilities that highlight issues and compliance.
How do I choose the best vulnerability management tool for my business?
Those looking for a vulnerability management tool should ask questions such as:
- What platforms does the tool operate on? Be aware that some are focused on Linux, some on Windows, and some cover multiple or all OS and platforms. Also take into account what staff are already trained on. Don’t add Linux tools if your internal personnel are trained on Windows, and vice-versa.
- What endpoints are covered? Some deal mainly with servers, PCs, and laptops, while others extend to smartphones, IoT, wireless, and other devices.
- Which parts of the security landscape are you looking to add or upgrade beyond vulnerability management? If you are in the midst of a complete overhaul of your entire security infrastructure, start with the suite and then find one that includes the vulnerability management features you need. But if you already have a solid security backbone, focus on vulnerability management tools that provide the coverage you need.
- Pay attention to the fine print in contrasts and look closely at cost structure, the potential for additional fees, support costs, etc.
- Don’t be stuck on one vendor for all security needs. Vendor A may work for most of your security infrastructure, but Vendor B may be better at vulnerability management.
- What do analysts such as Gartner say about the different tools, their market share, their pros and cons, and future direction?
Whatever tool you choose from the list above, the benefits of vulnerability management quickly show up in terms of fewer breaches, data that is better safeguarded, attacks being spotted far earlier than before, and added automation.
Methodology
The tools covered here were selected based on analyst reports, peer reviews, and user satisfaction, as well as reviews posted in TechRepublic and other Technology Advice sites. I also provided a mix of full-fledged vulnerability management products, highly specialized tools, and those where vulnerability management is one module within a much larger suite.
[ad_2]
Source link



