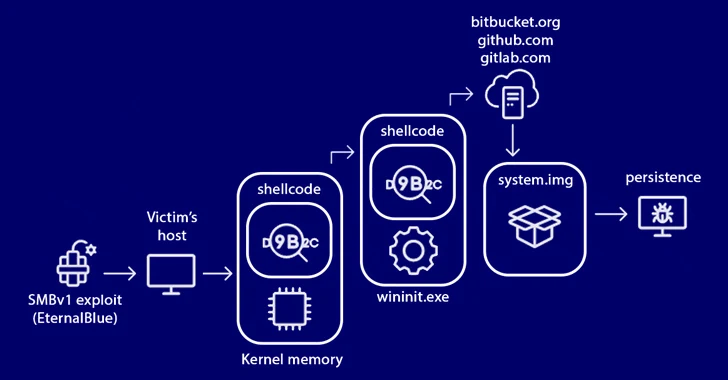
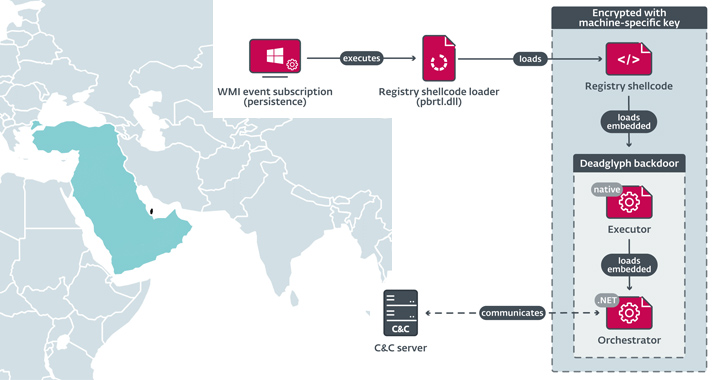
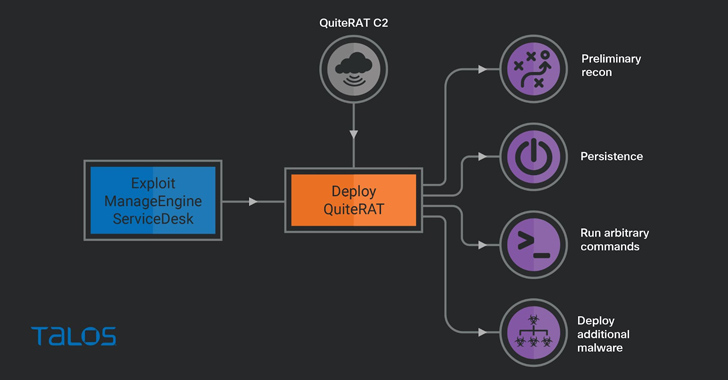
Nov 11, 2023NewsroomThreat Intelligence / Cybercrime A sub-cluster within the infamous Lazarus Group has established new infrastructure that impersonates skills assessment portals as part of its social engineering campaigns. Microsoft attributed the activity to a threat actor it calls Sapphire Sleet, describing it as a “shift in the persistent actor’s tactics.” Sapphire Sleet, also called […]
StripedFly Malware Operated Unnoticed for 5 Years, Infecting 1 Million Devices
An advanced strain of malware masquerading as a cryptocurrency miner has managed to fly the radar for over five years, infecting no less than one million devices around the world in the process. That’s according to findings from Kaspersky, which has codenamed the threat StripedFly, describing it as an “intricate modular framework that supports both […]